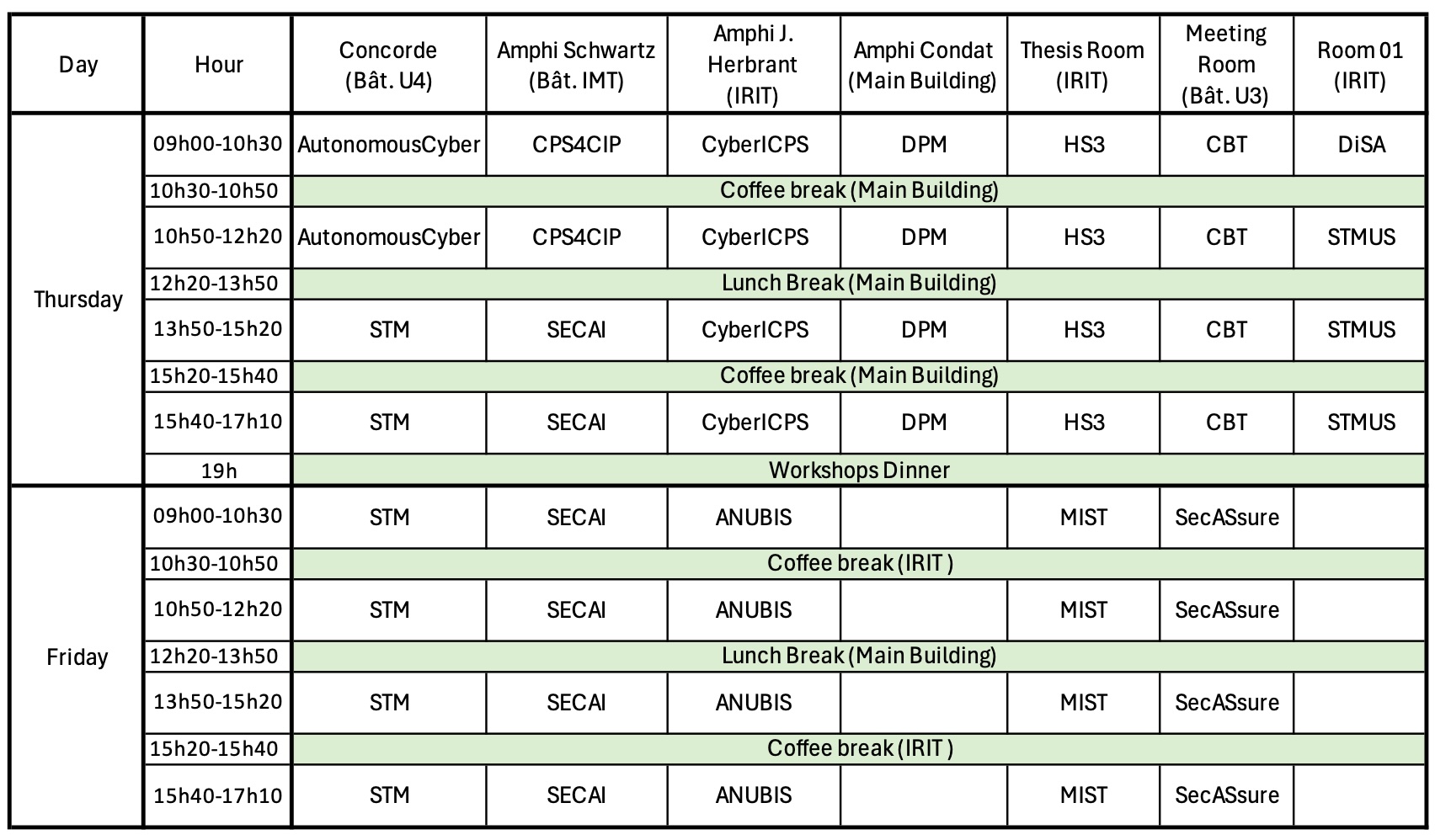
Workshop Schedule
Workshops program at glance
Map
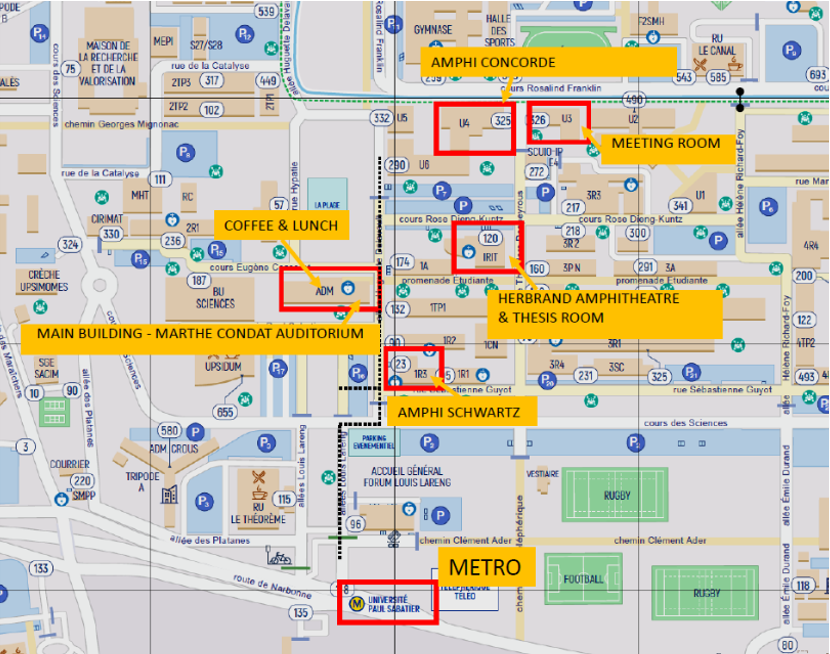
GPS positions of the buildings (Google map)
Bât U3 (CBT, SecAssure) - Click here
Bât U4 (AutonomousCyber, STM) - Click here
IRIT Building (ANUBIS, CyberICPS, DiSA, HS3, MIST, STMUS) - Click here
- Amphi J. Herbrant, Thesis Room and Room 001
IMT Building (CPS4CIP, SECAI) - Click here
Main Building (DPM) - Click here
Workshops detailled program
ANUBIS
Friday 26 September
09h00-10h30
- Keynote: Digital Twins for Cyberdefense, Cristina Alcaraz
- No Bot Allowed: Detection of Automated Traffic on Modern Booking Platforms. Methods, Insights, and Current Challenges, Umberto Fontana, Elisa Chiapponi, Claudio Costanza, Vincent Rigal, Olivier Thonnard, Martynas Buozis and Herve Debar
10h30-10h50 Coffee break
10h50-12h20 Session
- HENDRICS: A Hardware-in-the-Loop Testbed for Enhanced Intrusion Detection, Response and Recovery of Industrial Control Systems, Lalie Arnoud, Zoé Lagache, Pierre-Henri Thevenon, Aloïs Champenois, Victor Breux, Maxime Puys, Eric Gaussier and Oum-El-Kheir Aktouf
- Get out of DEDALE with RESCOUSSE: a New Dataset and Testbed for Evaluating the Detection of APT attacks among Network and System Logs, Maxime Lanvin and Frédéric Majorczyk
- Superviz25-SQL: High-Quality Dataset to Empower Unsupervised SQL Injection Detection Systems, Grégor Quetel, Eric Alata, Pierre-François Gimenez, Laurent Pautet and Thomas Robert
12h20-13h50 Lunch Break
13h50-15h20 Session
- Middlebox Assessment and Network Gaps: Observing Enforced Security, Alya Alshaikh, Ilies Benhabbour and Marc Dacier
- Network Intrusion Response Systems: Towards standardized evaluation of intrusion response, Thomas Marchioro, Rachida Saroui and Alexis Olivereau
- Nxcap: A Unified Format for NIDS Benchmarking, Gabin Noblet, Cédric Lefebvre, Philippe Owezarski and William Ritchie
15h20-15h40 Coffee break
15h40-17h10 Session
- Synthetic Network Traffic Generation for Intrusion Detection Systems: a Systematic Literature Review, Pierre-François Gimenez
- Constraint-based Network Topology Generation for Evaluating Federated Intrusion Detection Systems, Léo Lavaur, Fabien Autrel and Yann Busnel
AutonomousCyber
Thursday 25 September
09h00-10h30 Session
- Welcome and Opening Remarks
- ACSE-Eval: Can LLMs threat model real-world cloud infrastructure?, Sarthak Munshi, Swapnil Pathak, Sonam Ghatode, Thenuga Priyadarshini, Dhivya Chandramouleeswaran and Ashutosh Rana
- Adversarial Evasion against Autonomous Cyber Defence Agents, Melanie Meijer, Sanyam Vyas, Vasilios Mavroudis and Marc Juarez
- Knowledge Retention for Generic Reinforcement Learning Policies in Autonomous Cyber Defence, Joshua Sylvester and Rogério de Lemos
- Automated Cyber Defence with Reinforcement Learning in Multi-Attack Environments, Joshua Sylvester and Rogério de Lemos
10h30-10h50 Coffee break
10h50-12h20 Session
- An Explainable Multimodal Framework for Phishing Attack Detection, Shokooh Khandan, Mohammadreza Tabatabaei, Ifeanyi Bryan Uzoatu, Olamide Jogunola, Yakubu Tsado and Tooska Dargahi
- Risk-Aware SOC Alert Handling in Adaptive Cyber Defense with Reinforcement Learning, Sajad Homayoun
- Leveraging Large Language Models in Post-Exploitation: Navigating the Cyber Kill Chain with AI-Driven Tactics, Dean Benson and Christo Panchev
CBT
Thursday 25 September
09h15-10h30
- Welcome and opening remarks (⚠️ Amphi Condat, Main Building)
Bart preneel - joint keynote with DPM workshop (Amphi Condat, main building)
10h30-10h50 Coffee Break
10h50-12h20 Session 1 (Bât. U3)
- Fast Off-Chain Payments with Second-Layer Privacy, Sven Gnap, Kari Kostiainen and Ghassan Karame
- AUPCH: Auditable Unlinkable Payment Channel Hubs, Mohsen Minaei, Pedro Moreno-Sanchez, Srinivasan Raghuraman, Panagiotis Chatzigiannis and Duc Le
- Threshold Signatures for Central Bank Digital Currencies, Mostafa Abdelrahman, Filip Rezabek, Lars Hupel, Kilian Glas and Georg Carle
12h20-13h50 Lunch Break (Main Building)
13h50-15h20 Session 2 (Bât. U3)
- Blockchain-Based Lotteries via Single Secret Leader Election, Tegrid Fettuh and Oğuz Yayla
- Towards a Resource Based Blockchain E-Voting System, Ricardo Almeida, Laura Ricci, Fabrizio Baiardi, Damiano Maesa, Catalin Dragan and Nishanth Sastry
- Analysing the Adoption of Terms of Use in SSI Digital Wallets, Stefano Bistarelli, Chiara Luchini and Francesco Santini
15h20-15h40 Coffee Break
15h40-17h10 Session 3 (Bât. U3)
- Multiple Selfish Miners on Nakamoto's Consensus Fruitchain, and Strongchain - An Empirical Evaluation, Martin Perešíni, Tomáš Hladký, Jakub Kubík and Ivan Homoliak
- EVMpress: Precise Type Inference for Next-Generation EVM Decompilation, Jung Hyun Kim, Soomin Kim, Jaeseung Choi and Sang Kil Cha
CPS4CIP
Thursday 25 September
09h00-10h30 Session
- Welcome and Opening Remarks
- A Comparative Study of ICS Honeypot Deployments, Frederik Ondrikov, Denis Donadel, Francesco Lupia, Massimo Merro, Daniel Ricardo dos Santos, Emmanuele Zambon and Nicola Zannone
- Learning-in-the-Middle: Explicit-Recursion Anomaly Detection for Critical Infrastructures, Peyman Teymoori and Toktam Ramezanifarkhani
- Integration of an OT cybersecurity lab into an industrial automation lab, Alejandro Manuel López Gómez, Farid Bagheri-Gisour Marandyn, Jaime Mohedano, Atanasio Carrasco, Agustín Valencia, José Antonio Rodríguez-Mondejar, Roberto Gesteira-Miñarro, Néstor Rodríguez Pérez, Rafael Palacios, Javier Jarauta and Gregorio López López
- Designing a NIS2-Compliant Registry System: A Design Science Approach to the Classification and Supervision of Essential and Important Entities, Fabian Aude Steen, Vasileios Mavroeidis, Mateusz Zych and Konstantinos Fysarakis
10h30-10h50 Coffee break
10h50-12h20 Session
- SecureIoT: Robust AI-Driven Cyber Threat Detection for IoT Applications, Knut Selstad, Sandeep Pirbhulal, Habtamu Abie, Riku Lehkonen and Ismail Ari Ari
- AI-Guided Test Case Prioritization from Network Traffic in Cyber-Physical Systems, Valeria Valdés Ríos, Fatiha Zaïdi and Ana Rosa Cavalli
- Improving Machine Learning Models for URL Phishing Detection using Synthetic Data, Francisco Cardoso, Eva Maia and Isabel Praça
- Federated Learning: An approach with Hybrid Homomorphic Encryption, Pedro Correia, Ivan Costa, Ivone Amorim, Eva Maia and Isabel Praça
- Conclusion & Planning
CyberICPS
Thursday 25 September
09h15-10h30 Welcome and opening remarks (⚠️ Amphi Condat, Main building)
Bart preneel - joint keynote with DPM workshop (Amphi Condat, Main building)
10h30-10h50 Coffee break
10h50-12h20 Session 1 (Amphi J. Herbrant, IRIT) - Chair: Sokratis Katsikas
- Salty Seagull: A VSAT Honeynet to Follow the Bread Crumb of Attacks in Ship Networks, Georgios Michail Makrakis, Jeroen Pijpker, Remco Hassing, Rob Loves and Stephen McCombie
- Signals and Symptoms: ICS Attack Dataset from Railway Cyber Range, Anis Yusof, Yuancheng Liu, Niklaus Kang, Choon Meng Seah, Zhenkai Liang and Chang Ee-Chien
- Designing and Testing a Low-Cost Electromagnetic Spectrum Attack Threat Monitoring System, Vassilis Andrianopoulos, Panayiotis Kotzanikolaou and Christos Douligeris
12h25-13h50 Lunch Break (Main building)
13h50-15h20 Session 2 (Amphi J. Herbrant, IRIT) - Chair: Frédéric Cuppens
- Detecting Anomalous Resource Consumption in Edge AI-Based MQTT Brokers,Phi Tuong Lau and Stefan Katzenbeisser
- CRLF: A Sim2Real Reinforcement Learning Environment for Automated IT/OT Pentesting, Marc-Antoine Faillon, Julien Francq, Frédéric Cuppens, Nora Boulahia-Cuppens and Reda Yaich
- From Words to Wires: Leveraging LLMs for Rapid ICS Cyber-Range Construction, Tommy Berg, Ahmed Amro, Aida Akbarzadeh and Georgios Kavallieratos
15h20-15h40 Coffee break
15h40-17h10 Session 3 (Amphi J. Herbrant, IRIT) - Chair: Nora Cuppens-Boulahia
- In Numeris Veritas: An Empirical Measurement of Wi-Fi Integration in Industry, Vyron Kampourakis, Christos Smiliotopoulos, Vasileios Gkioulos and Sokratis Katsikas
- Using Dual Algorithm Certificates in TLS: Enabling Rapid Transition to Post-Quantum Cryptography with Backward Compatibility,Tobias Frauenschläger and Juergen Prof. Dr. Mottok
- Secure and Efficient Attribute-based Signature Scheme for Substation Automation Systems, Mohammed Ramadan, Moritz Gstür, Pranit Gadekar, Ghada Elbez and Veit Hagenmeyer
DiSA
Thursday 25 September
09h00-10h30 Session
- short welcome
- Protecting Society from Fake Advertisement Campaigns: Innovative Graph Based Analysis and Approach, Ewelina Bartuzi-Trokielewicz, Alicja Martinek, Rafał Kozik, Michał Choraś
- Adapting Epidemic Contact Models to Misinformation Spread via Social Networks, Lankeshwara Munasinghe and Christopher Mcdermott
- POLfake: relational dataset for Polish fake news detection, Mateusz Walczak, Aneta Poniszewska-Maranda
- Transparent and Trustworthy eXpainable AI (xAI) in Smart Human-Robot Collaboration Environment, Michał Choraś, Aleksandra Pawlicka, Marek Pawlicki, Rafal Kozik
DPM
Thursday 25 September
09h15-10h30
- Welcome and opening remarks (Amphi Condat, Main Building)
Bart Preneel - joint keynote (Amphi Condat, Main Building)
10h30-10h50 Coffee break (Main Building)
10h50-12h25 Session 1 (Amphi Condat, Main Building), session chair Ken Barker (University of Calgary)
- How Worrying Are Privacy Attacks Against Machine Learning?, Josep Domingo-Ferrer
- Lost in the Averages: Reassessing Record-Specific Privacy Risk Evaluation, Yves-Alexandre de Montjoye, Natasa Krco, Matthieu Meeus, Bogdan Kulynych
- Membership Inference Attacks Beyond Overfitting, Mona Khalil, Alberto Blanco-Justicia, Najeeb Jebreel, Josep Domingo-Ferrer
- "Why is the sky blue?" – On the feasibility of privacy-friendly conversational LLM smart toys, Isabel Wagner, Valentyna Pavliv, Luigi Lazri, Jan Buechele
- Win-k: Improved Membership Inference Attacks on Small Language Models, M. Emre Gursoy, Roya Arkhammadova, Hosein Madadi Tamar
12h25-13h50 Lunch Break (Main Building)
13h50-15h20 Session 2 (Amphi Condat, Main Building), session chair Guillermo Navarro-Arribas (Universitat Autonoma de Barcelona)
- Advanced Electronic Signatures and GDPR: Reconciling the Concepts,Miroslaw Kutylowski, Paweł Kostkiewicz, Gabriel Wechta
- Invisible Encryption, Shahzad Ahmad, Stefan Rass, Zahra Seyedi
- Eliminating Exponential Key Growth in PRG-Based Distributed Point Functions, Marc Damie, Florian Hahn, Andreas Peter, Jan Ramon
- A Pseudo-Inverse Matrix-Based LDP for High-Dimensional Data, Hiroaki Kikuchi
- Using Prior Knowledge to Improve GANs for Tabular Data Without Compromising Privacy, Sonakshi Garg, Marcel Neunhoeffer, Jörg Drechsler, Vicenc Torra
15h20-15h40 Coffee break (Main Building)
15h40-17h10 Session 3 (Amphi Condat, Main Building), session chair Joaquin Garcia-Alfaro (Institut Polytechnique de Paris)
- Lessons from a Robotaxi: Challenges in Selecting Privacy-Enhancing Technologies, Sebastian Pape, Ala’A Al-Momani, David Balenson, Christoph Bösch, Zoltán Ádám Mann, Jonathan Petit
- Performance Analysis of Lightweight Transformer Models for Healthcare Application Privacy Threat Detection, Jude Ameh, Abayomi Otebolaku, Alex Shenfield, Augustine Ikpehai, Dauda Sule
- The Bitter Pill: Tracking and Remarketing on EU Pharmacy Websites, Zahra Moti, Kimberley Frings, Christine Utz, Frederik Zuiderveen Borgesius, Gunes Acar
- PADOME: Adaptive Privacy Assistant for the Internet of Things, Edward Rochester, Ken Barker
H3S
Thursday 25 September
9h00-10h30 Session 1: Attacks & Vulnerabilities
- OpenGL GPU-Based Rowhammer Attack, Antoine Plin, Frédéric Fauberteau and Nga Nguyen
- Cache Attacks in Modern/Multi-socket x86 Systems (Work in Progress), Guillaume Didier, Augustin Lucas and Thomas Rokicki
- Revealing Embedded System Behaviors: A Comparative Analysis of Power Consumption and Hardware Performance Counters, Mohammed Mezaouli, Yehya Nasser, Samir Saoudi and Marc-Oliver Pahl
- Germany Is Rolling Out Nation-Scale Key Escrow And Nobody Is Talking About It, Jan Sebastian Götte
10h30-10h50 Coffee Break
10h50-12h20 Session 2: Defences & Anomaly Detection
- Hardware Performance Counters for Anomaly Detection in Embedded Devices, Victor Breux and Pierre-Henri Thevenon
- Semantic-Aware Provenance-Based Intrusion Detection for Edge Systems, Qingyu Zeng, Songxuan Liu, Yu Wu and Yuko Hara
- Inter-Device PUFs: A Novel Paradigm for Physical Unclonable Functions, Emiliia Geloczi and Stefan Katzenbeisser
- Mitigation of the impact of Virtual Machine Introspection Pauses on Multi-core Virtual Machines, Léo Cosseron, Louis Rilling and Martin Quinson
12h20-13h50 Lunch Break
13h50-15h20 Session 3: Invited Talk
- Hardware-software co-design for security with CHERIoT: from memory-safety to software supply-chain resilience, Robert Norton
13h50-15h40 Coffee Break
15h40-16h30 Session 4: Verification and Validation
- heRVé: towards a formally verified RISC-V processor with security mechanisms (Work in Progress), Cyprien Jules, Pierre Wilke, Guillaume Hiet and Gabriel Desfrene
- InSight - A CoreSight Trace Interpreter for Dynamic Information Flow Tracking (Work in Progress), Quentin Ducasse, Guillaume Hiet, Volker Stolz and Pierre Wilke
16h30 Open Discussion & Closing
MIST
Friday 26 September
9h-10h30 Session 1
- Welcome speech + Keynote
- Streamlining Security Patches and Remote Attestations for the Internet of Things, Konrad-Felix Krentz
10h30-10h50 Coffee break (20mn)
10h50-12h20 Session 2
- Lightweight IoT Intrusion Detection with Hybrid Feature Selection and CNN-Driven Image Transformation, Negar Mansouri, Seyedeh Leili Mirtaheri, Seyyed Amir Asghari and Andrea Pugliese
- Breaking the Silence: Fuzzing LTE-M and NB-IoT protocols, Ilja Siroš, Rafael Cavalcanti, Dave Singelée and Bart Preneel
- Function-Level Syscall Fingerprinting for IoT Malware Capability Classification, Yutaro Osako, Hayato Hamano, Yuto Aono, Toshihiro Yamauchi, Katsunari Yoshioka, Takahiro Kasama, Takuya Fujihashi and Shunsuke Saruwatari
- Permission Granted? How Android’s App List Protection Fails in Practice, Julian Gagel, Kris Heid and Jens Heider
12h20-13h50 Lunch Break (1h30)
13h50-15h20 Session 3
- Revisiting the Effectiveness of Jailbreak Detection, Muhammad Irfan and Nelson Uto
- PIM: A Metric to Empower Mobile App Users in Privacy Management, Amador Aparicio, M. Mercedes Martínez-González, Alejandro Pérez-Fuente and Pablo A. Criado-Lozano
- Policy Enforcement Protocols with Split Keys, Gizem Akman, Philip Ginzboorg, Sampo Sovio and Valtteri Niemi
- Closing
15h20-15h40 Coffee break (20mn)
SECAI
Thursday 25 September
13h50-14h00 Welcome
14h00-15h15 Session
- On the Effectiveness of Generative Adversarial Networks for data augmentation in malware detection, Giovanni Ciaramella, Fabio Martinelli, Antonella Santone and Francesco Mercaldo
- An Adaptive Self-guarded and Risk-Aware Honeypot using DRL, Sereysethy Touch and Jean-Noël Colin
- Simplicity Performs, But Should It? Examining Malware Detection Benchmark Datasets, Samy Bettaieb, Laurens D'hooge, Charles-Henry Bertrand Van Ouytsel, Axel Legay, Etienne Rivière, Miel Verkerken and Bruno Volckaert
15h15-15h35 Coffe Break
15h35-17h10 Session
- One Size Doesn't Fit All: A Dynamic Heterogeneous Learning Ensemble for Malware Family Classification, Solomon Sonya, Muqi Zou, Saastha Vasan, Christopher Kruegel, Giovanni Vigna and Dongyan Xu
- Evaluating The Explainability of Deep Learning-based Network Intrusion Detection Systems, Ayush Kumar and Vrizlynn Thing
- In-context learning for the classification of manipulation techniques in phishing emails, Antony Dalmiere, Guillaume Auriol, Vincent Nicomette and Pascal Marchand
- Evaluating the Capabilities of AI-based Penetration Testing Tools, Jacques Ophoff, Ibeabuchi Egbu and Sanaz Kavianpour
Friday 26 September
09h00-10h35
- Diffusion or Non-Diffusion Adversarial Defenses: Rethinking the Relation between Classifier and Adversarial Purifier, Yuan-Chih Chen and Chun-Shien Lu
- Scalable Generation of Invariance-Based Adversarial Examples Using XAI, Samuel Oberhofer, Martin Nocker, Florian Merkle and Pascal Schöttle
- Analysing Safety Risks in LLMs Fine-Tuned with Pseudo-Malicious Cyber Security Data, Adel Elzemity, Budi Arief and Shujun Li
- Towards a Systematic Risk Assessment of Deep Neural Network Limitations in Autonomous Driving Perception, Svetlana Pavlitska, Christopher Gerking and J. Marius Zöllner
10h35-10h55 Coffe Break
10h55-12h10
- Backdoor Attacks on Transformers for Tabular Data: An Empirical Study, Bart Pleiter, Behrad Tajalli, Stefanos Koffas, Gorka Abad, Jing Xu, Martha Larson and Stjepan Picek
- Strategic Sample Selection for Improved Clean-Label Backdoor Attacks in Text Classification, Onur Alp Kirci and M. Emre Gursoy
- Towards Automated Threat Elicitation from the AI Act, Simone Di Mauro, Mario Raciti and Giampaolo Bella
12h10-13h50 Lunch Break
13h50-15h50
- Methodology for Systematic Security Testing of LLM-based Applications, Dawid Nastaj and Wojciech Mazurczyk
- Adaptive Token-Weighted Differential Privacy for LLMs: Not All Tokens Require Equal Protection, Manjiang Yu, Priyanka Singh, Xue Li and Yang Cao
- Does Retrieval-Augmented Generation Mitigate Training Data Leakage Risks from Large Language Models?, Tsunato Nakai, Takuya Higashi and Kento Oonishi
- From Legacy to Standard: LLM-Assisted Transformation of Cybersecurity Playbooks into CACAO Format, Mehdi Akbari Gurabi, Lasse Nitz, Radu-Mihai Castravet, Roman Matzutt, Avikarsha Mandal and Stefan Decker
- Prompt Infection: LLM-to-LLM Prompt Injection within Multi-Agent Systems, Donghyun Lee, Mo Tiwari and Brando Miranda
15h50-16h00 Best Paper Award and Closing
SecAssure
Friday 26 September
09h30-10h30 Join keynote session with STM (⚠️ Amphi Concorde, Bât U4)
- Should I trust or should I go? A deep dive into the (not so reliable) web PKI trust model, Romain Laborde
10h30-10h50 Coffee break (20mn)
10h50-12h20 Session 2: Cloud & Microservices Security Assurance, Chair: Ankur Shukla
- Noisy Neighbor: Exploiting RDMA for Resource Exhaustion Attacks in Containerized Clouds, Gunwoo Kim, Taejune Park and Jinwoo Kim
- ConLock: Reducing Runtime Attack Surface in Containerized Microservices, Asbat El Khairi, Andreas Peter and Andrea Continella
- Towards Zero-Knowledge Based Private and Verifiable Software Assurance, Karl Norrman, Björn Johansson and Ferhat Karakoc
12h20-13h50 Lunch Break (1h30)
13h50-15h20 Session 3: Policy, Compliance & Threat Assurance, Chair: Sandeep Pirbhulal
- Assessing the State of Proactive Data Usage Control Enforcement, Monika Kamhuber, Sascha Wessel and Joana Pecholt
- Modelling Offensive Security Killchains from Compliance Gaps with Security Directives, Gianpietro Castiglione and Giampaolo Bella
- Security Management of Threats with CyberGraph, Ettore Carbone, Paolo Falcarin, Purbasha Chowdhury, Francesco Bruno and Fabio Dainese
15h20-15h40 Coffee break (20mn)
15h40-17h10 Session 4: Group Discussion and Closing Remarks
- Group Discussion: Security Assurance and Emergency Technologies: Challenges and Innovations
STM
Thursday 25 September
13h30-13h45 Welcome session
13h45-14h45 ERCIM STM AWARD 2025 Presentation
- Cyber-Physical Anomaly Detection for Industrial Control Systems: two novel frameworks and an Intrusion Response System, Simone Guarino
14h45-15h00 Coffee/tea break
15h00-17h00 Session 1: Identity Manag., Authentication, Access Control & Formal Modeling
- Toward Secure and Trustworthy Identity Management Systems: A Knowledge-base Driven Approach, Gianluca Sassetti, Amir Sharif, Roberto Carbone and Silvio Ranise
- Always Authenticated, Never Exposed: Continuous Authentication via Zero-Knowledge Proofs, Dennis Hamm, Erwin Kupris and Thomas Schreck
- Pragmatic guidelines for formal modeling of security ceremonies, Barbara Fila and Ermenda Hoxha
- Access Control Administration for Smart Homes, Clara Bertolissi and Maribel Fernandez
Friday 26 September
9h30-10h30 Keynote Session
- Should I trust or should I go? A deep dive into the (not so reliable) web PKI trust model, Romain Laborde
10h30-10h50 Coffee break (20mn)
10h50-12h20 Session 2: AI & Machine Learning For Security (Session Chair: Cristina Alcaraz)
- Parameter-Efficient Fine-Tuning of LLMs for Intrusion Detection and Firewall Rule Generation: A Comparative Study, Chi Zhang, Muhammad Shadi Hajar, Harsha Kalutarage and Lankeshwara Munasinghe
- ABusing social media & sentiment analysis for stock market prediction, Crawford Brown, Nikolaos Pitropakis, Christos Chrysoulas and Costas Lambrinoudakis
- DrATC+: A Divide et Impera Extension to Trust-Based Dynamic Routing, Davide Ferraris, Letizia Russo and Lorenzo Monti
12h20-13h50 Lunch Break
13h50-15h20 Session 3: Cybersecurity Strategies, Regulations, Privacy Session
- How to Train Your Guardian: Evaluating Cyber Security Exercises Using Situation Awareness, Håvard J. Ofte and Sokratis Katsikas
- Towards an architecture for managing security under the EU Cyber Resilience Act, Daniele Canavese, Afonso Ferreira, Romain Laborde and Mohamed Ali Kandi
- Google Tag Manager and its Privacy Issues, Javiera Alegría Dinamarca, Ivana Bachmann and Javier Bustos-Jiménez
15h20-15h30 Coffee/Tea Break
15h30-17h00 Session 4: Cryptography & Threat Analysis
- Measuring Modern Phishing Tactics: A Quantitative Study of Body Obfuscation Prevalence, Co-occurrence, and Filter Impact, Antony Dalmiere, Zheng Zhou, Guillaume Auriol, Vincent Nicomette and Pascal Marchand
- Nicknames for Group Signatures, Guillaume Quispe, Pierre Jouvelot and Gérard Memmi
- The Impact of Filtering in Differential Cryptanalysis: A Case Study on FEAL-8, Ivan Costa, Ivone Amorim, Eva Maia and Isabel Praça
17h00-17h10 Closing Session
STMUS
Thursday 25 September
11h00-11h15 Opening Remarks
11h15-12h15 Session
- Overview of Machine Unlearning in Fostering Responsible and Adaptive AI in Education Context. Betty Mayeku, Sandra Hummel and Parisa Memarmoshrefi
- Adversarial Federated Unlearning with Representation Decoupling.Yu Jiang, Kwok-Yan Lam and Chee Wei Tan
12h15-13h50 Lunch Break
14h00-15h00 Session
- Machine Unlearning of Multilingual Transformers for Kazakh Text Classification. Milana Bolatbek and Shynar Mussiraliyeva
15h00-15h30 Coffee Break
15h30-16h00 Session
- When Forgetting Reveals: Black-Box Inversion Attacks on Unlearning in Large Language Models. Zijun Zhang, Bang Wu and Xingliang Yuan
16h00-16h50 Discussion (Participants: TBD)
16h50-17h00 Concluding Remarks
|




